On Monday May 15, the Nitra Faculty Hospital was still dealing with the aftermath of a massive malware attack from Friday afternoon. Only around half of its computers were in working order on Monday morning, while the rest were being checked and gradually brought back into operation, hospital spokesperson Tatiana Timková told the TASR newswire on the same day.
However, the computer blackout has not jeopardised the treatment of patients, stressed Timková. Nonetheless, patients had to be prepared for somewhat longer waiting times due to the complications with the computers.
No sensitive data was leaked during the attack.
"Some damage has been caused, however, so we're considering filing a criminal complaint against an unknown perpetrator," said Timková as cited by TASR. "We're consulting with a lawyer about this option at the moment."
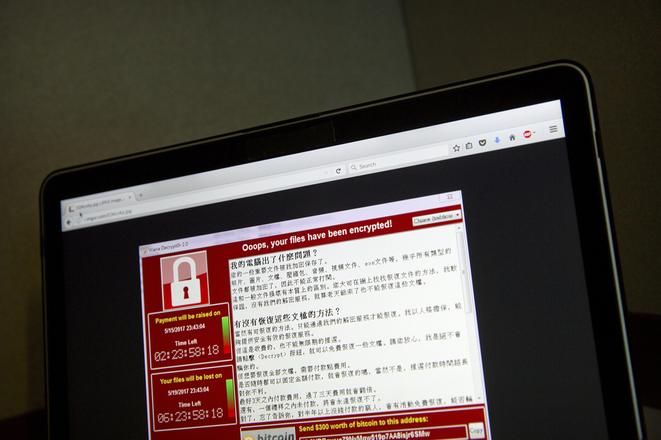
The screens of the computers at the Nitra Faculty Hospital suddenly turned red shortly after noon on Friday, May 12.
"An order was released immediately to shut down all computers and the situation was tackled right away," said Timková. "The malware was identified and is still being removed."
Only a few in Slovakia
In Slovakia only a few companies were infected by the ransomware Wannacry, informed Zuzana Hošalová, spokesperson of the security software company Eset. She stressed that companies are not obliged to report such cases but as of May 2018 companies in the EU member countries will be obliged to report each leakage of any personal data, including those caused by malware.
The malware that hit computers in dozens of countries worldwide on May 12 is a later version of the ransomware that occured in February 2017.
An infection usually gets into companies through the financial, personnel or marketing departments, as their workers are used to getting e-mails from unknown addresses. After infection, the ransomware encodes the content of the device and asks for a ransom, stated Hošalová.
“The ransom of 300 dollars is relatively low," said Hošalová, adding that paying the ransom does not always mean getting the code to unlock the data. “If the device was already encoded it is hard to get the data back."
The security experts search for mistakes in the code to get the decoding key, summed up Hošalová, adding that the decryptolocker to Wannacry is not available world-wide.
The Wannacry malware especially infects computers that use the Windows XP operational system that is no longer supported by Microsoft. Some companies and organisations are still using Windows XP for financial reasons or because it is too complicated and sometimes almost technically impossible to change to another one.
Microsoft released updates for supported versions of its operational system to protect it against this threat in March.